After part 3, I had a fully-functioning, switched network. So then why would I want to change that? Ah, because if it ain’t broke, you aren’t doing it right. As I stated before, ACL-based firewalls are limited, defining only inbound, outbound, and local (to the router) rules on each interface. I didn’t like that limitation, since it wasn’t granular enough for those VLAN-to-VLAN connections. Fortunately, though, EdgeOS has the capability to get as strict as you want, but you better be ready for some CLI configurations!
The secret is Zone Policies, which allow you to define different zones based on interface or VLAN, and then state exactly what interactions you want to allow and disallow between those zones. To start with, I followed this tutorial, which sets up a very straightforward set of zones. I didn’t use VLANs at the router interface, instead using the WLAN, LAN, WAN, and Local zones I had started with, but it worked well enough.
The thing to remember about zone firewall rules is that you need to define them for each pair of zones, from one to another. A consistent naming schema is important, so this is what I settled on:
Image may be NSFW.
Clik here to view.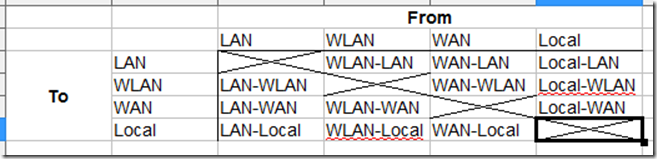
Note that this will double if you include IPv6 rules; more on that later!
So if you follow that tutorial, you’ll notice that the default action is always drop. That’s the safest action to take with packets that don’t meet any explicit rules. I also enable logging of those default drops to figure out if they need to be allowed. Block all, enable later: that’s the most secure plan of action.
In the tutorial, the first two rules are to allow established sessions, and block invalid connections. I kept those. It suggests a pattern for the remaining rules, which I tweaked a bit. Remember, rules run from 1 to the end, so you want the highly-utilized rules first and the less-utilized rules last to cut down on processing time. This is what I settled on:
|
Rule |
Description |
|
100 |
DNS |
|
200 |
HTTP/HTTPS |
|
300 |
Syslog |
|
400 |
NTP |
|
500 |
SSH |
|
600 |
ICMP |
|
700 |
DHCP |
|
800 |
IMAP/POP3/SMTP |
|
900 |
Other |
That doesn’t include rules 1 and 2, plus the default drop. Of course, when I set up these rules for each zone-to-zone rule, I only added the appropriate rules. I’m not going to allow Syslog from the WAN to any internal zone, for example, so that wasn’t included.
In the end, after much tweaking, I got the below rule and zone set. How did I figure out what was being blocked? That’s where Splunk came in handy. In Part 5, I’ll talk about how I used Splunk to analyze these rules. In the meantime, here is what I set up:
all-ping enable
broadcast-ping disable
group {
}
name LAN-WAN {
default-action drop
description "Wired LAN to WAN Firewall"
enable-default-log
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
log enable
state {
invalid enable
}
}
rule 100 {
action accept
description "DNS Allow"
destination {
port 53
}
log enable
protocol tcp_udp
}
rule 200 {
action accept
description "HTTP/S Allow"
destination {
port 80,443
}
log enable
protocol tcp
}
rule 400 {
action accept
description "NTP Allow"
destination {
port 123
}
log enable
protocol udp
}
rule 600 {
action accept
log enable
protocol icmp
}
rule 800 {
action accept
description "IMAP Allow"
destination {
port 993
}
log enable
protocol tcp
}
rule 900 {
action accept
description "Google Talk Allow"
destination {
port 5222
}
log enable
protocol tcp
}
rule 910 {
action accept
description "MSN Chat Allow"
destination {
port 1863
}
log enable
protocol tcp
}
rule 920 {
action accept
description "Yahoo Messenger Enable"
destination {
port 5050
}
log enable
protocol tcp
}
rule 930 {
action accept
description "AOL/ICQ Enable"
destination {
port 5190
}
log enable
protocol tcp
}
rule 940 {
action accept
description "Steam Enable"
destination {
port 27014-27050
}
log enable
protocol tcp
}
rule 950 {
action accept
description "Google Play/Cloud Enable"
destination {
port 5228
}
log enable
protocol tcp
}
}
name LAN-WLAN {
default-action drop
description "Wired LAN to Wireless LAN Firewall"
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
log enable
state {
invalid enable
}
}
rule 300 {
action accept
description "Syslog Allow"
destination {
port 514
}
protocol udp
}
rule 600 {
action accept
log enable
protocol icmp
}
}
name Local-LAN {
default-action drop
description "Router to Wired LAN Firewall"
enable-default-log
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
log enable
state {
invalid enable
}
}
}
name Local-WAN {
default-action drop
description "Router to WAN Firewall"
enable-default-log
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
log enable
state {
invalid enable
}
}
rule 100 {
action accept
description "DNS Allow"
destination {
port 53
}
log enable
protocol tcp_udp
}
rule 400 {
action accept
description "NTP Allow"
destination {
port 123
}
log enable
protocol udp
}
rule 700 {
action accept
description "DHCP Allow"
destination {
port 67
}
log enable
protocol udp
}
}
name Local-WLAN {
default-action drop
description "Router to Wireless LAN Firewall"
enable-default-log
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
log enable
state {
invalid enable
}
}
rule 300 {
action accept
description "Syslog Allow"
destination {
port 514
}
protocol udp
}
rule 600 {
action accept
description "ICMP Allow"
log enable
protocol icmp
}
rule 701 {
action accept
description "DHCP Allow"
destination {
port 68
}
log enable
protocol udp
source {
port 67
}
}
}
name WAN-LAN {
default-action drop
description "WAN to Wired LAN Firewall"
enable-default-log
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
log enable
state {
invalid enable
}
}
}
name WAN-Local {
default-action drop
description "WAN to Router Firewall"
enable-default-log
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
log enable
state {
invalid enable
}
}
rule 701 {
action accept
description "DHCP Allow"
destination {
port 68
}
log enable
protocol udp
source {
port 67
}
}
}
name WAN-WLAN {
default-action drop
description "WAN to Wireless LAN Firewall"
enable-default-log
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
log enable
state {
invalid enable
}
}
}
name WLAN-LAN {
default-action drop
description "Wireless LAN to Wired LAN Firewall"
enable-default-log
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
log enable
state {
invalid enable
}
}
rule 200 {
action accept
description "HTTP/S Allow"
destination {
port 80,443
}
log enable
protocol tcp
}
rule 500 {
action accept
description "SSH Allow"
destination {
port 22
}
log enable
protocol tcp
}
rule 600 {
action accept
protocol icmp
}
rule 900 {
action accept
description "BOINC Allow"
destination {
port 31416
}
log enable
protocol tcp
}
rule 910 {
action accept
description "TightVNC Allow"
destination {
port 5901-5910
}
log enable
protocol tcp
}
}
name WLAN-Local {
default-action drop
description "Wireless LAN to Router Firewall"
enable-default-log
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
log enable
state {
invalid enable
}
}
rule 100 {
action accept
description "DNS Allow"
destination {
port 53
}
log enable
protocol tcp_udp
}
rule 200 {
action accept
description "HTTP/S Allow"
destination {
port 80,443
}
log enable
protocol tcp
}
rule 500 {
action accept
description "SSH Allow"
destination {
port 22
}
log enable
protocol tcp
}
rule 600 {
action accept
description "ICMP Allow"
protocol icmp
}
}
name WLAN-WAN {
default-action drop
description "Wireless LAN to WAN Firewall"
enable-default-log
rule 1 {
action accept
state {
established enable
related enable
}
}
rule 2 {
action drop
log enable
state {
invalid enable
}
}
rule 100 {
action accept
description "DNS Allow"
destination {
port 53
}
log disable
protocol tcp_udp
}
rule 200 {
action accept
description "HTTP/S Allow"
destination {
port 80,443
}
log enable
protocol tcp
}
rule 400 {
action accept
description "NTP Allow"
destination {
port 123
}
log enable
protocol udp
}
rule 600 {
action accept
description "ICMP Allow"
log enable
protocol icmp
}
rule 800 {
action accept
description "IMAP Allow"
destination {
port 993
}
log enable
protocol tcp
}
rule 900 {
action accept
description "Google Talk Allow"
destination {
port 5222,5223
}
log enable
protocol tcp
}
rule 910 {
action accept
description "MSN Chat Allow"
destination {
port 1863
}
log enable
protocol tcp
}
rule 920 {
action accept
description "Yahoo Messenger Enable"
destination {
port 5050
}
log enable
protocol tcp
}
rule 930 {
action accept
description "AOL/ICQ Enable"
destination {
port 5190
}
log enable
protocol tcp
}
rule 940 {
action accept
description "Steam Client Allow"
destination {
port 27000-27030
}
log enable
protocol udp
}
rule 941 {
action accept
description "Steam Download Allow"
destination {
port 27014-27050
}
log enable
protocol tcp
}
rule 950 {
action accept
description "Google Play/Cloud Enable"
destination {
port 5228
}
log enable
protocol tcp
}
}
receive-redirects disable
send-redirects enable
source-validation disable
syn-cookies enable
}
zone-policy {
zone LAN {
default-action drop
description "LAN Zone"
from Local {
firewall {
name Local-LAN
}
}
from WAN {
firewall {
name WAN-LAN
}
}
from WLAN {
firewall {
name WLAN-LAN
}
}
interface eth0
}
zone Local {
default-action drop
from LAN {
firewall {
name LAN-Local
}
}
from WAN {
firewall {
name WAN-Local
}
}
from WLAN {
firewall {
name WLAN-Local
}
}
local-zone
}
zone WAN {
default-action drop
description "WAN Zone"
from LAN {
firewall {
name LAN-WAN
}
}
from Local {
firewall {
name Local-WAN
}
}
from WLAN {
firewall {
name WLAN-WAN
}
}
interface eth2
}
zone WLAN {
default-action drop
from LAN {
firewall {
name LAN-WLAN
}
}
from Local {
firewall {
name Local-WLAN
}
}
from WAN {
firewall {
name WAN-WLAN
}
}
interface eth1
}
}
- Current Mood: Calm
- Currently Listening To: "All Of You", Miles Davis


